Incident Response Checklist Templates
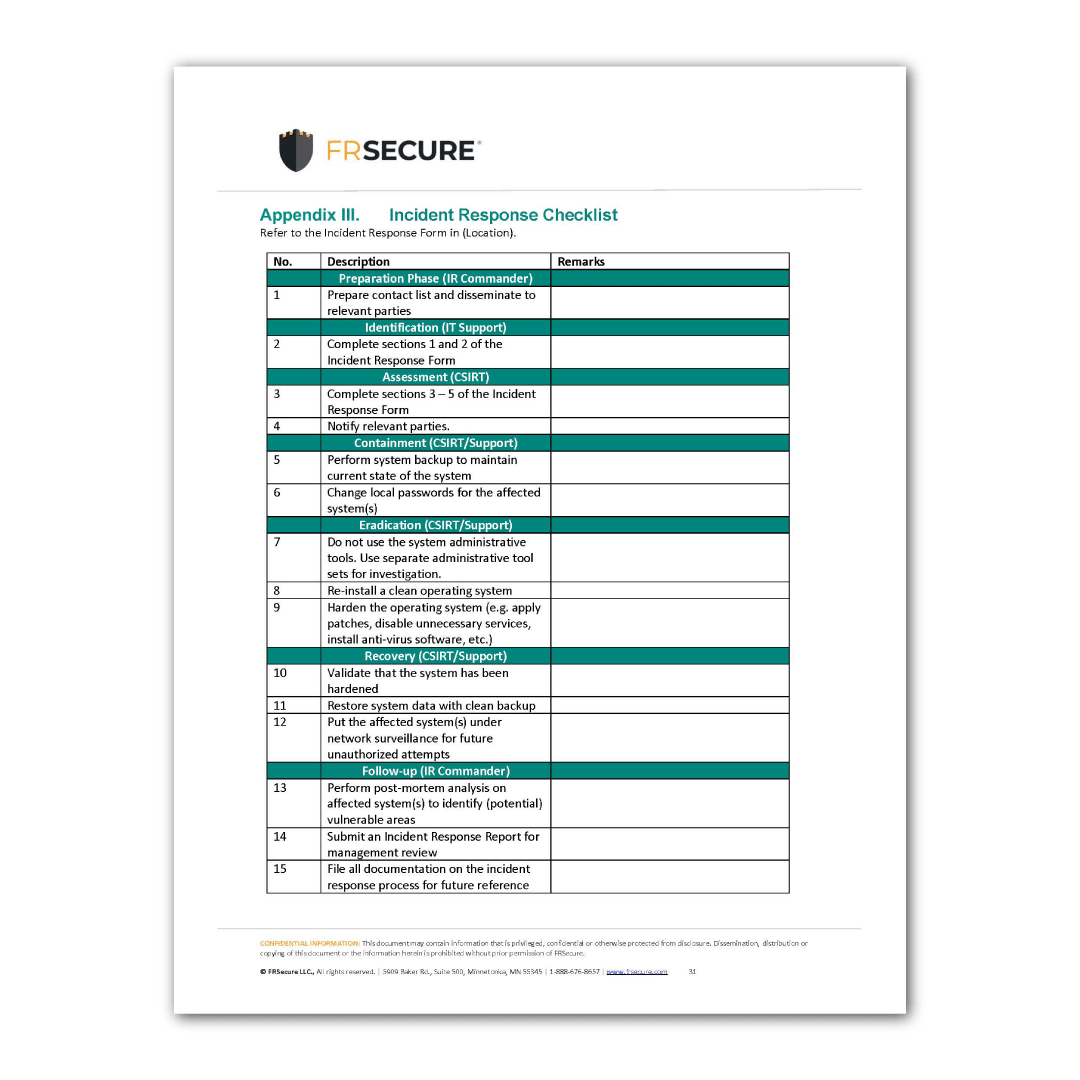
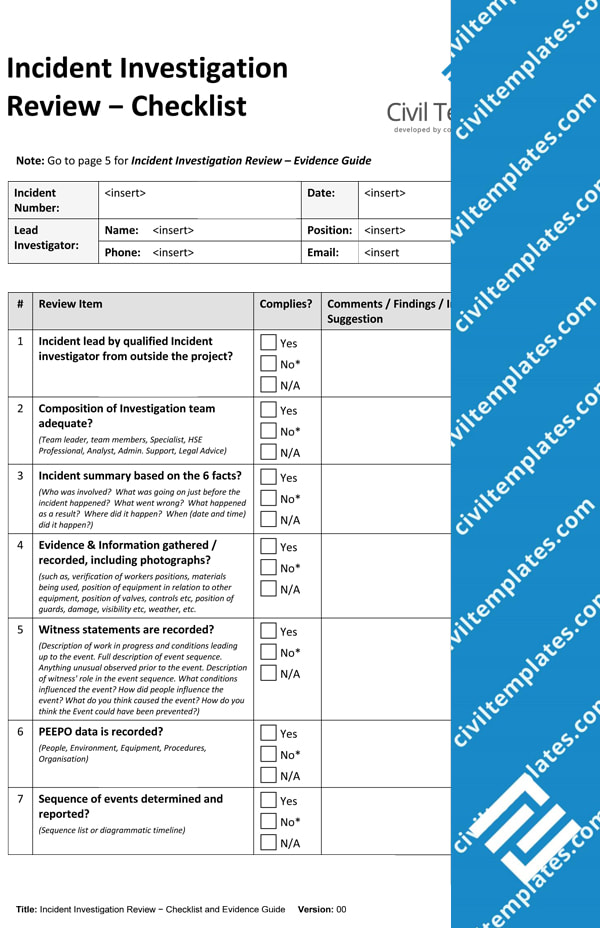
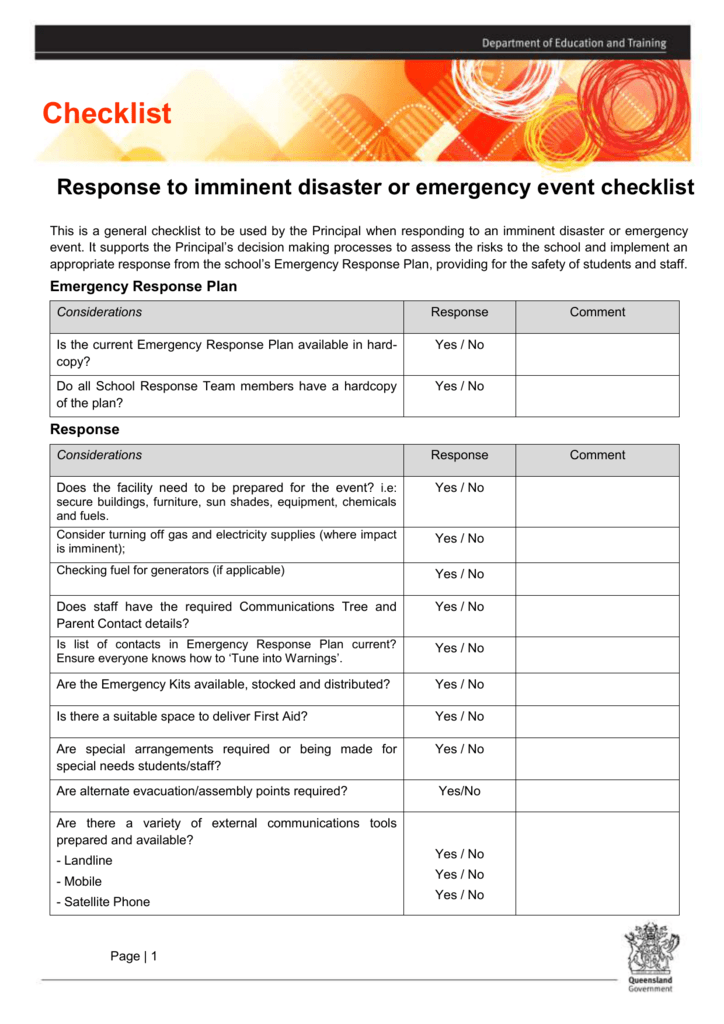
Incident Response Checklist Templates - Writing an effective cybersecurity incident report is a critical step in incident response. This incident response plan checklist provides a comprehensive overview of the necessary steps to take when responding to a security incident. How to build an incident response plan around the 6 phases of incident response, examples to get you started, and a peek at incident response automation. When a privacy or information security incident occurs, it is imperative that the agency follow documented procedures for responding to and processing the incident. Incident response team roles and responsibilities. Define an incident response plan; Learn how to create an incident response plan with these templates from nist, nasa, berkeley university, and more. Cyber security incident response (ir) is a set of information security policies and procedures used to prepare, detect, contain and recover data from any breach. What should be included in an incident response checklist? Creating a cybersecurity incident response checklist requires an understanding of the security threats that a company may face, as well as an understanding of how to respond to those. Begin the attestation process step 1: Being prepared for data breaches is part of a robust compliance program. An effective incident response playbook is comprised of several key components to ensure a structured and efficient response to cybersecurity incidents: It outlines the processes needed to. What should be included in an incident response checklist? Dora’s article 5 requires organizations to establish effective. Incident response team roles and responsibilities. Incident response and breach management. Cyber security incident response (ir) is a set of information security policies and procedures used to prepare, detect, contain and recover data from any breach. It is a best practice to have an incident response plan developed an implemented. It is a best practice to have an incident response plan developed an implemented. Writing an effective cybersecurity incident report is a critical step in incident response. Being prepared for data breaches is part of a robust compliance program. This incident report checklist is specifically designed for professionals in the construction industry to comprehensively capture incident details, assess the severity. These stages form a systematic approach to handling. Cyber security incident response (ir) is a set of information security policies and procedures used to prepare, detect, contain and recover data from any breach. Begin the attestation process step 1: An established incident response plan ensures that data breaches are handled swiftly and efficiently. Incident response team roles and responsibilities. It is a best practice to have an incident response plan developed an implemented. When a privacy or information security incident occurs, it is imperative that the agency follow documented procedures for responding to and processing the incident. Defining incident response team roles and responsibilities is essential in the incident handling checklist to ensure clarity,. As you develop a standardized. In this article, we look at 12 incident response plan templates. Learn how to create an incident response plan with these templates from nist, nasa, berkeley university, and more. What is an incident response. Dora checklist template serves as a methodical tool to evaluate major regulatory needs throughout zones encompassing ict risk governance as well as operational resilience. Audits should. It is a best practice to have an incident response plan developed an implemented. Creating a cybersecurity incident response checklist requires an understanding of the security threats that a company may face, as well as an understanding of how to respond to those. What should be included in an incident response checklist? How to build an incident response plan around. These stages form a systematic approach to handling. It outlines the processes needed to. Cyber security incident response (ir) is a set of information security policies and procedures used to prepare, detect, contain and recover data from any breach. An incident response checklist should include information on how to identify the incident, how to contain the incident, how to. Begin. It is a best practice to have an incident response plan developed an implemented. An effective incident response playbook is comprised of several key components to ensure a structured and efficient response to cybersecurity incidents: Dora’s article 5 requires organizations to establish effective. As you develop a standardized process for incident management, templates can be a powerful tool to help. Cyber security incident response (ir) is a set of information security policies and procedures used to prepare, detect, contain and recover data from any breach. When a privacy or information security incident occurs, it is imperative that the agency follow documented procedures for responding to and processing the incident. Audits should verify the existence and. Dora’s article 5 requires organizations. An incident response checklist should include information on how to identify the incident, how to contain the incident, how to. Defining incident response team roles and responsibilities is essential in the incident handling checklist to ensure clarity,. An effective incident response playbook is comprised of several key components to ensure a structured and efficient response to cybersecurity incidents: Audits should. What should be included in an incident response checklist? It outlines the processes needed to. Begin the attestation process step 1: How to build an incident response plan around the 6 phases of incident response, examples to get you started, and a peek at incident response automation. An established incident response plan ensures that data breaches are handled swiftly. Incident response team roles and responsibilities. This incident report checklist is specifically designed for professionals in the construction industry to comprehensively capture incident details, assess the severity of the event, analyze. When a privacy or information security incident occurs, it is imperative that the agency follow documented procedures for responding to and processing the incident. Cyber security incident response (ir) is a set of information security policies and procedures used to prepare, detect, contain and recover data from any breach. Writing an effective cybersecurity incident report is a critical step in incident response. It outlines the processes needed to. Incident response plan templates provide a framework you can customize to your organization's unique situation. How to build an incident response plan around the 6 phases of incident response, examples to get you started, and a peek at incident response automation. What should be included in an incident response checklist? This incident response plan checklist provides a comprehensive overview of the necessary steps to take when responding to a security incident. Creating a cybersecurity incident response checklist requires an understanding of the security threats that a company may face, as well as an understanding of how to respond to those. An incident response checklist should include information on how to identify the incident, how to contain the incident, how to. In this article, we look at 12 incident response plan templates. It is a best practice to have an incident response plan developed an implemented. What is an incident response. Being prepared for data breaches is part of a robust compliance program.Incident Response Plan Template
Incident Response Checklist Templates
IT Incident Response Checklist Template in Word, PDF, Google Docs
Incident Response Checklist Templates
Incident Response Checklist Templates
Incident Response Checklist Templates
Security Incident Response Plan Template
Incident Response Checklist Templates
Incident Response Checklist Templates
Incident Response Checklist Templates
Dora Checklist Template Serves As A Methodical Tool To Evaluate Major Regulatory Needs Throughout Zones Encompassing Ict Risk Governance As Well As Operational Resilience.
Defining Incident Response Team Roles And Responsibilities Is Essential In The Incident Handling Checklist To Ensure Clarity,.
These Stages Form A Systematic Approach To Handling.
Dora’s Article 5 Requires Organizations To Establish Effective.
Related Post: