Nist Csf Policy Templates
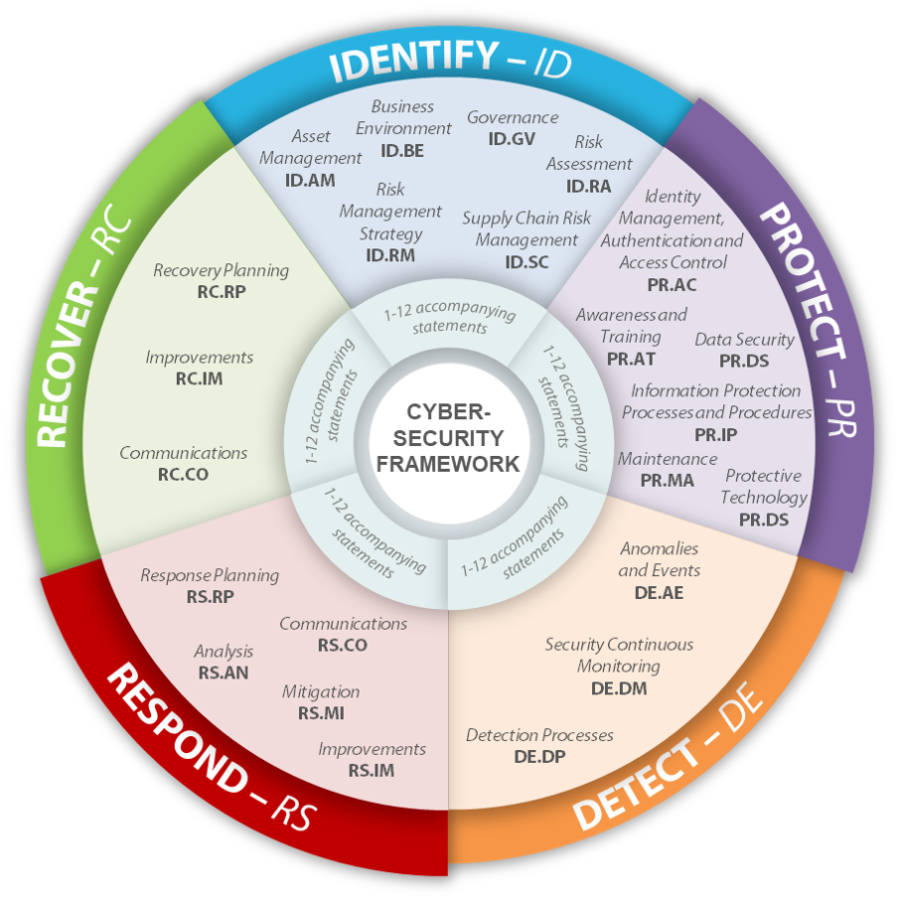
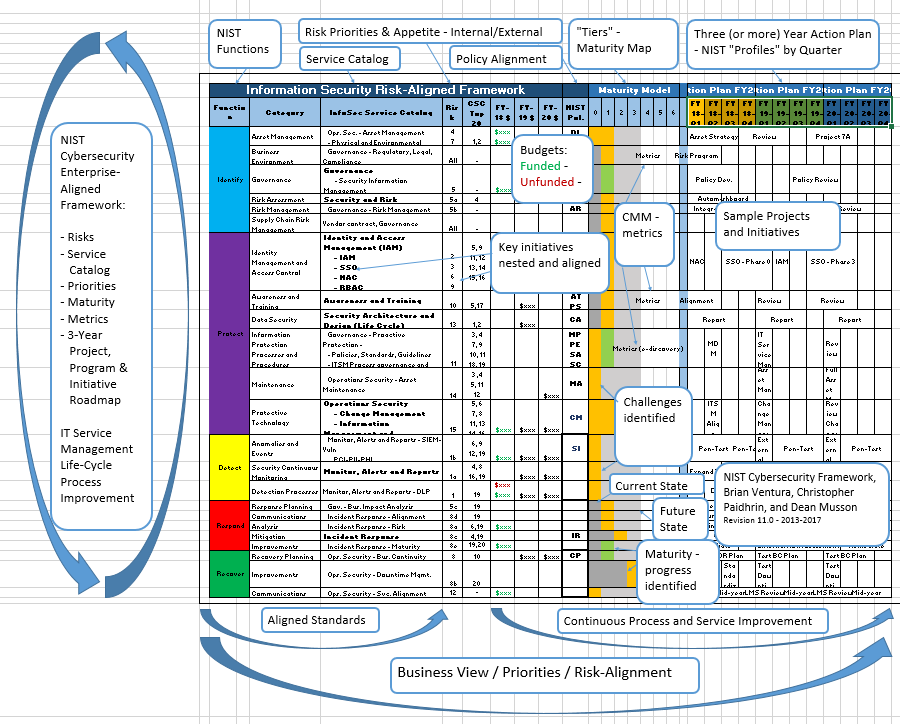
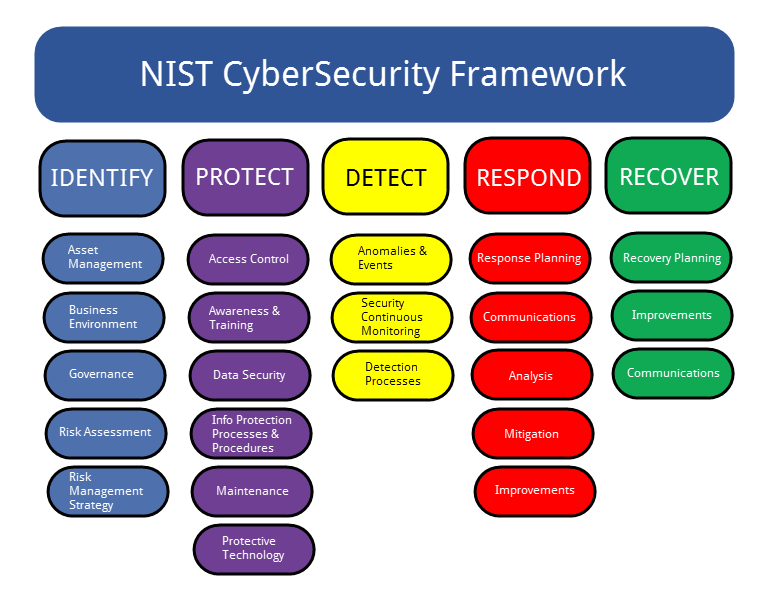
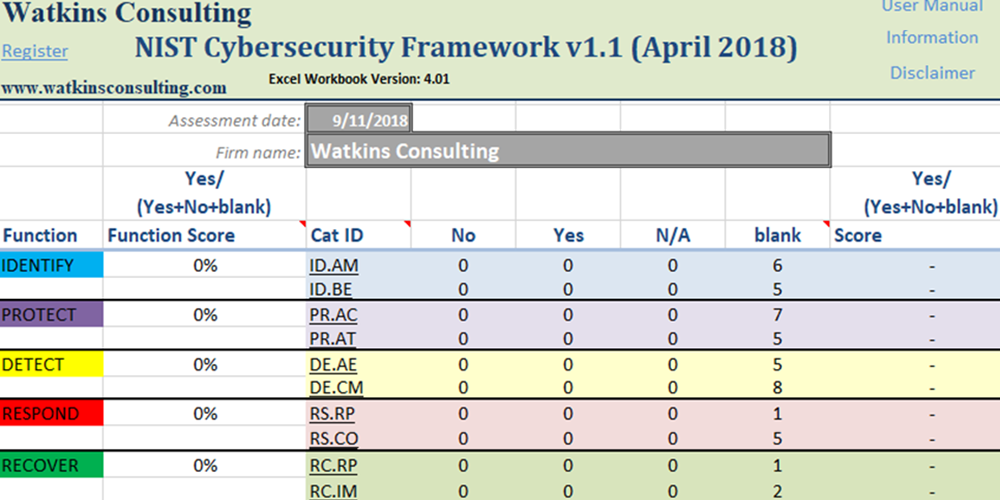
Nist Csf Policy Templates - Use this template to simplify the process of developing a nist csf 2.0. Organizations seeking to reduce cyber risk and meet compliance requirements often. Resources include, but are not limited to: Nist cybersecurity framework policy template guide. Download nist csf+, built by sans instructor brian ventura, a framework management tool. Nist provides a csf organizational profile template as a microsoft excel spreadsheet. 172 in terms of outcomes identified in the csf. Ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. The free cybersecurity policy templates provided by this site can be downloaded as individual templates that are organized by the nist cybersecurity framework 2.0 core functions and. View the quick start guides. The free cybersecurity policy templates provided by this site can be downloaded as individual templates that are organized by the nist cybersecurity framework 2.0 core functions and. Your guide to help reduce cyber risk and ease compliance readiness with modernized identity security. Framework version 1.1 (pdf) framework version 1.1 core (excel) translations; Nist cybersecurity framework policy template guide. Attackers may also steal an. Csf 1.1 archive expand or collapse. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. The national institute of standards technology (nist) cybersecurity framework provides a policy framework of computer security guidance for how private sector organizations can. For industry, government, and organizations to reduce cybersecurity risks. View the quick start guides. View the quick start guides. For users with specific common goals. This article delves into the components of the nist cybersecurity framework, outlines the importance of a policy template, and offers a comprehensive guide on drafting an. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. Csf 2.0 resource center expand or collapse. Organizations seeking to reduce cyber risk and meet compliance requirements often. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. Nist cybersecurity framework policy template guide. Periodically provide risk reporting to leaders about how acquired components are proven to be untampered and authentic. Use this template to simplify the process of developing a nist csf 2.0. Framework version 1.1 (pdf) framework version 1.1 core (excel) translations; This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. The document outlines the five main functions within the nist csf (identify, protect, detect, respond, recover), listing subcategories within each along with relevant policy templates. Nist provides a csf organizational profile template. This guide gives the correlation between 35 of the nist csf subcategories, and applicable sans policy. Periodically provide risk reporting to leaders about how acquired components are proven to be untampered and authentic. You can download it and fill it in to create current and target profiles for your organization. This article delves into the components of the nist cybersecurity. Organizations seeking to reduce cyber risk and meet compliance requirements often. An access control policy defines how your organization manages user access to systems, data, and applications. You can download it and fill it in to create current and target profiles for your organization. Nist provides a csf organizational profile template as a microsoft excel spreadsheet. Your guide to help. This article delves into the components of the nist cybersecurity framework, outlines the importance of a policy template, and offers a comprehensive guide on drafting an. Complianceforge nist cybersecurity framework compliance documentation templates. The document outlines the five main functions within the nist csf (identify, protect, detect, respond, recover), listing subcategories within each along with relevant policy templates. Examples of. Download nist csf+, built by sans instructor brian ventura, a framework management tool. Examples of profiles can be found on the nist csf 173 website along with a template for creating organizational profiles. Resources include, but are not limited to: View the quick start guides. 172 in terms of outcomes identified in the csf. Users can download 36 policy templates aligned with each nist csf 2.0 core function. For users with specific common goals. Use this template to simplify the process of developing a nist csf 2.0. Download free policy and standard templates for the nist csf 2.0 identify core function, which focuses on understanding the organizational environment and the risks to its systems,. This guide gives the correlation between 35 of the nist csf subcategories, and applicable sans policy. Download nist csf+, built by sans instructor brian ventura, a framework management tool. Ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. For users with specific common goals. The free cybersecurity policy templates provided. Resources include, but are not limited to: Your guide to help reduce cyber risk and ease compliance readiness with modernized identity security. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. For users with specific common goals. The free cybersecurity policy templates provided by this site can be downloaded as individual. The national institute of standards technology (nist) cybersecurity framework provides a policy framework of computer security guidance for how private sector organizations can. Resources include, but are not limited to: Attackers may also steal an. Complianceforge nist cybersecurity framework compliance documentation templates. Download (pdf) quick start guides; An access control policy defines how your organization manages user access to systems, data, and applications. For users with specific common goals. The document outlines the five main functions within the nist csf (identify, protect, detect, respond, recover), listing subcategories within each along with relevant policy templates. The free cybersecurity policy templates provided by this site can be downloaded as individual templates that are organized by the nist cybersecurity framework 2.0 core functions and. Framework version 1.1 (pdf) framework version 1.1 core (excel) translations; Nist provides a csf organizational profile template as a microsoft excel spreadsheet. This article delves into the components of the nist cybersecurity framework, outlines the importance of a policy template, and offers a comprehensive guide on drafting an. Use this template to simplify the process of developing a nist csf 2.0. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. View the quick start guides. Csf 2.0 resource center expand or collapse.NIST CSF 2.0 Policy Template
Nist Cybersecurity Framework Policy Templates
Nist Csf Policy Templates
Nist Csf Policy Templates
Policy Template Guide NIST Cybersecurity Framework PDF Security
NIST Cybersecurity Framework Policy Template Guide 2024 Nist Cloud
Cybersecurity & Data Privacy Policies & Standards Templates
Nist Cybersecurity Framework Template
Cyber Security Risk Assessment Template Nist
SOLUTION Nist csf policy template guide 2020 0720 1 iso iec 27001
Ransomware Is A Type Of Malicious Attack Where Attackers Encrypt An Organization’s Data And Demand Payment To Restore Access.
172 In Terms Of Outcomes Identified In The Csf.
Examples Of Profiles Can Be Found On The Nist Csf 173 Website Along With A Template For Creating Organizational Profiles.
This Guide Gives The Correlation Between 35 Of The Nist Csf Subcategories, And Applicable Sans Policy.
Related Post: