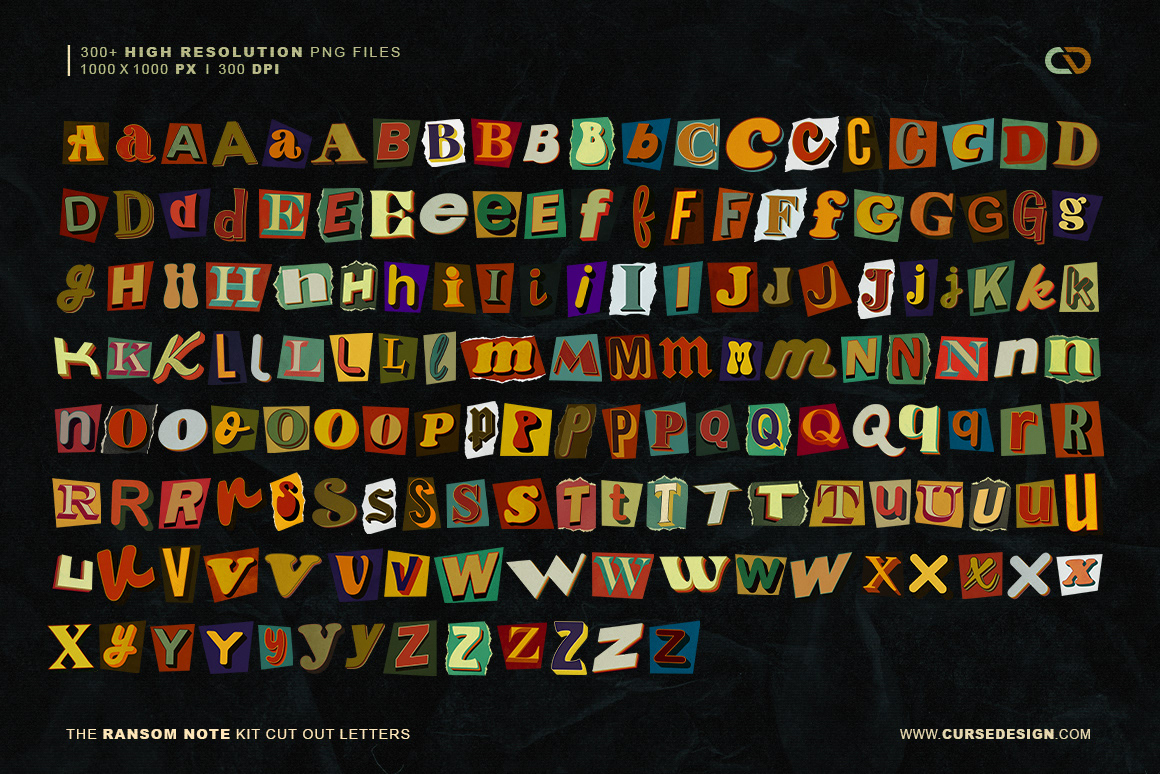Ransom Poster Template
Ransom Poster Template - Ransomware is a type of malicious software (a.k.a malware) that cyber criminals use to extort money from organizations. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. This large poster summarizes the three layers of protection and mitigation between. Create free ransomware protection flyers, posters, social media graphics and videos in minutes. Explore professionally designed ransom photo templates you can customize and share from playground. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. Create free ransom flyers, posters, social media graphics and videos in minutes. When activated, ransomware encrypts information stored on your. A ransomware attack occurs when hackers gain control over data or a computer system and hold it hostage until a ransom is paid. Looking to create that vintage. A ransomware attack occurs when hackers gain control over data or a computer system and hold it hostage until a ransom is paid. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. When activated, ransomware encrypts information stored on your. Ransomware is a type of malicious software (a.k.a malware) that cyber criminals use to extort money from organizations. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. Create free ransom flyers, posters, social media graphics and videos in minutes. Be cyber vigilant and don’t hand over your data to hackers. The ransomware and cyber extortion poster helps you and your organization prevent, detect, and hunt for ransomware and cyber extortion actors. Create free ransom flyers, posters, social media graphics and videos in minutes. Be cyber vigilant and don’t hand over your data to hackers. Create free ransom flyers, posters, social media graphics and videos in minutes. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. Explore professionally designed ransom photo templates you can customize and share from playground. This large poster summarizes the. Create free ransom flyers, posters, social media graphics and videos in minutes. Looking to create that vintage. The ransomware and cyber extortion poster helps you and your organization prevent, detect, and hunt for ransomware and cyber extortion actors. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. This large poster. Create free ransom flyers, posters, social media graphics and videos in minutes. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. Ransomware is a type of malicious software (a.k.a malware) that cyber criminals use to extort money from organizations. This large poster summarizes the three layers of protection and mitigation. Get online protection, secure cloud storage, and innovative apps designed to fit your needs—all in one plan. Be cyber vigilant and don’t hand over your data to hackers. This large poster summarizes the three layers of protection and mitigation between. Create free ransom flyers, posters, social media graphics and videos in minutes. Create free ransom flyers, posters, social media graphics. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. This large poster summarizes the three layers of protection and mitigation between. A ransomware attack occurs when hackers gain control over data or a computer system and hold it hostage until a ransom is paid. Ransomware is a type of malicious. Ransomware is a type of malicious software (a.k.a malware) that cyber criminals use to extort money from organizations. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. A ransomware attack occurs when hackers gain control over data or a computer system and hold it hostage until a ransom is paid.. Create free ransomware protection flyers, posters, social media graphics and videos in minutes. Explore professionally designed ransom photo templates you can customize and share from playground. Looking to create that vintage. When activated, ransomware encrypts information stored on your. A ransomware attack occurs when hackers gain control over data or a computer system and hold it hostage until a ransom. Be cyber vigilant and don’t hand over your data to hackers. Create free ransom flyers, posters, social media graphics and videos in minutes. Looking to create that vintage. A ransomware attack occurs when hackers gain control over data or a computer system and hold it hostage until a ransom is paid. Get online protection, secure cloud storage, and innovative apps. Explore professionally designed ransom photo templates you can customize and share from playground. Be cyber vigilant and don’t hand over your data to hackers. Get online protection, secure cloud storage, and innovative apps designed to fit your needs—all in one plan. Create free ransom flyers, posters, social media graphics and videos in minutes. Ransomware is a type of malicious software. Be cyber vigilant and don’t hand over your data to hackers. A ransomware attack occurs when hackers gain control over data or a computer system and hold it hostage until a ransom is paid. Explore professionally designed ransom photo templates you can customize and share from playground. When activated, ransomware encrypts information stored on your. This large poster summarizes the. This large poster summarizes the three layers of protection and mitigation between. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. When activated, ransomware encrypts information stored on your. A ransomware attack occurs when hackers gain control over data or a computer system and hold it hostage until a ransom is paid. Create free ransom flyers, posters, social media graphics and videos in minutes. Create free ransom flyers, posters, social media graphics and videos in minutes. Ransomware is a type of malicious software (a.k.a malware) that cyber criminals use to extort money from organizations. Explore professionally designed ransom photo templates you can customize and share from playground. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources. The ransomware and cyber extortion poster helps you and your organization prevent, detect, and hunt for ransomware and cyber extortion actors. Create free ransomware protection flyers, posters, social media graphics and videos in minutes. This large poster summarizes the three layers of protection and mitigation between ransomware attackers and your organization's ransomable resources.Ransom Note Discount Flyer Design Template Stock Vector Illustration
“Beware Ransomware!” Awareness Poster
Luxury deluxe Ransomware Background vector illustration. Abstract
Ransom Note Discount Flyer Design Template Vector Illustration
Ransom Note 300+ Cut Out Letters + Bonus Behance
Ransom Note Warriors Studio
Luxury deluxe Ransomware Background vector illustration. Abstract
Ransom Note Advertising Flyer Design Template Stock Illustration
seq_ransom_poster
Real colorful ransom style vector alphabet typeface clippings set with
Looking To Create That Vintage.
Be Cyber Vigilant And Don’t Hand Over Your Data To Hackers.
Get Online Protection, Secure Cloud Storage, And Innovative Apps Designed To Fit Your Needs—All In One Plan.
Related Post: